In a world where cyber‑attacks and data breaches are multiplying, the security of digital exchanges has become a strategic priority. Businesses and public authorities must protect their sensitive information from ever-more sophisticated threats. End-to-end encryption (E2EE) is an indispensable solution.
In this article, find out why end-to-end encryption is a cornerstone for ensuring confidentiality, security and sovereignty in your professional communications.
What is end-to-end encryption?
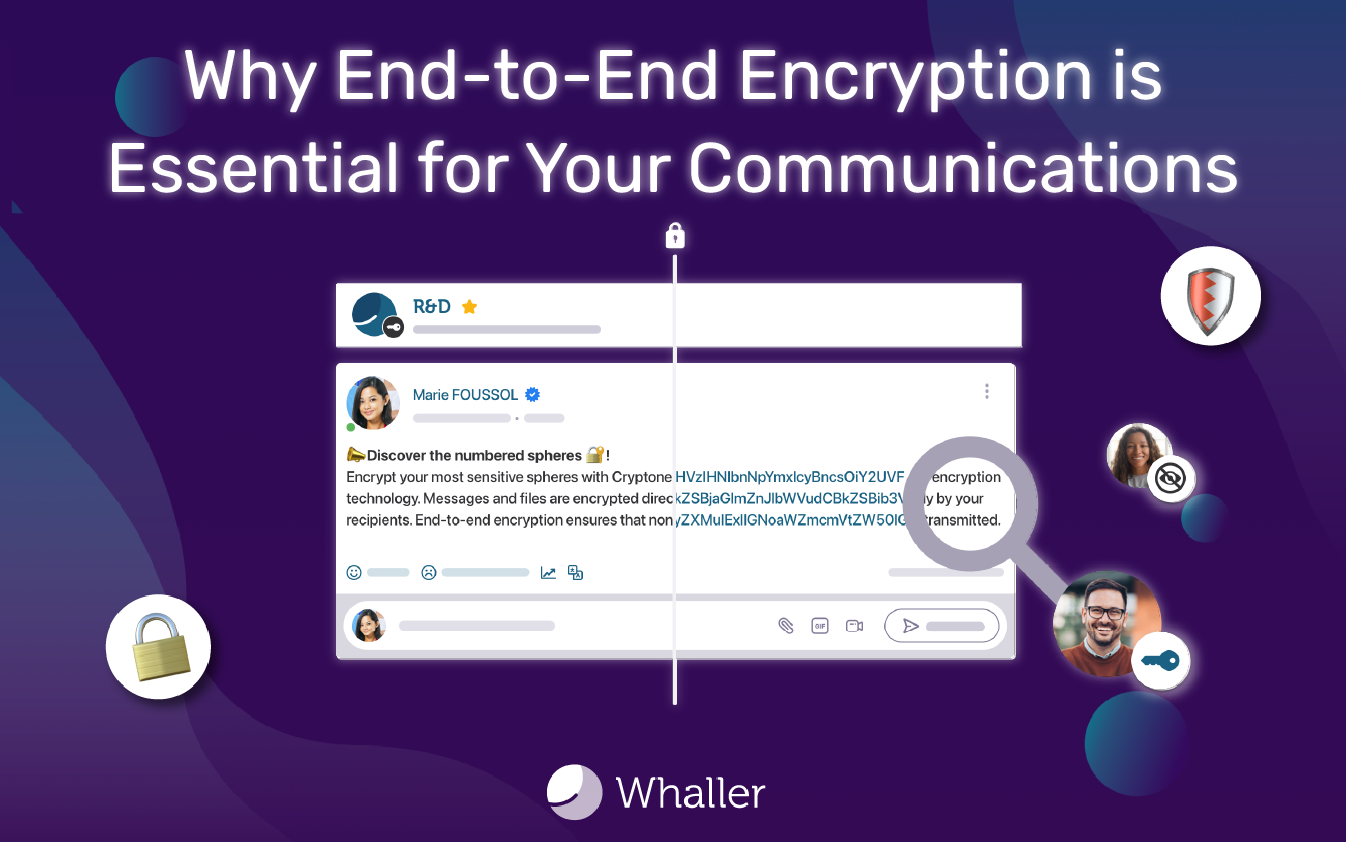
End-to-end encryption is based on a simple yet powerful concept: only the genuine sender and recipient can access the exchanged messages or files. It relies on cryptographic keys generated locally on users’ devices. Unlike traditional systems where data may be decrypted on intermediate servers, E2EE prevents any other party—including the platform provider—from accessing the information.
In practice, E2EE works as follows:
- Data is encrypted locally on the sender’s device with a unique key.
- This data remains encrypted in transit, preventing third-party reading.
- Only the recipient, with the corresponding private key, can decrypt and read the data.
This mechanism ensures that even if communications are intercepted, they remain completely unreadable to unauthorised parties.
Protection against modern cyber-threats
The risks associated with data breaches increase as digital communication intensifies. Cyber-attacks such as interceptions (so-called “man-in-the-middle” attacks), server compromises or accidental leaks are becoming commonplace.
End-to-end encryption acts as an impenetrable safeguard:
- Resistant to interception: even if data is captured in transit, it remains unreadable without the correct key.
- Protection against server compromise: even if a server is breached, the stored data remains unusable.
- Infrastructure-independent security: no need to trust any intermediary—security relies solely on the end users.
Technical challenges of end-to-end encryption
While E2EE is one of the most secure solutions available, it does pose technical challenges. Implementation requires advanced cryptographic expertise and suitable software architecture.
- Cryptographic key management: generating, sharing and securely storing keys is critical. Leading solutions, including Whaller’s, use proven standards like RSA for asymmetric encryption and AES‑256 for symmetric encryption.
- Safeguarding against failure points: mismanaging keys can lead to irreversible data loss. Some systems offer backup mechanisms such as “master keys” to restore access if needed.
- Performance and user experience: encryption can slow down exchanges if not optimised. Modern technologies, like Cryptoner (Whaller’s native encryption engine), ensure robust security without compromising usability.
A standard for digital sovereignty
End-to-end encryption does more than protect data from malicious actors—it also addresses digital sovereignty issues by ensuring information is inaccessible to service providers or foreign jurisdictions.
With laws such as the American Cloud Act enabling foreign authorities to request data stored on their servers, E2EE offers a simple solution: making data technically inaccessible to unauthorised entities, regardless of legal jurisdiction.
In Europe, initiatives like GDPR and the NIS2 directive recognise the importance of these security measures. By integrating E2EE at a fundamental level, organisations can comply with these requirements while demonstrating strong commitment to data protection.
Innovation through Cryptoner
Whaller has developed deep expertise in encryption. With its native technology Cryptoner, Whaller adapts E2EE principles to complex collaborative environments.
- Native encryption: unlike solutions requiring external integrations, Cryptoner is built into Whaller’s infrastructure from the ground up.
- Local key storage: encryption keys are generated and stored solely on users’ devices, ensuring no data can be accessed by Whaller or its servers.
- Compliant with ANSSI standards: although CSPN certification is planned for 2025, the algorithms already meet the recommendations of France’s national cybersecurity agency.
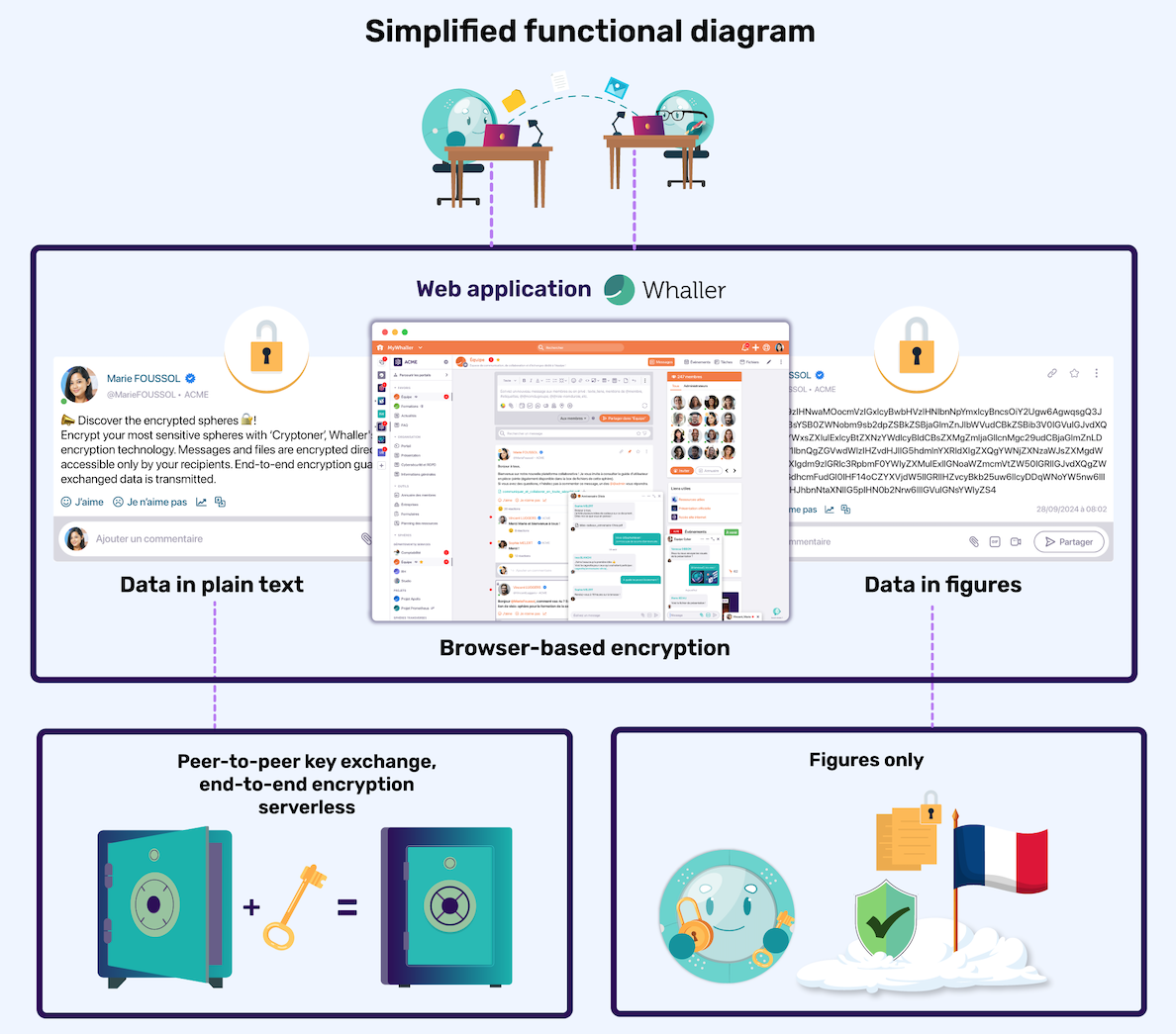
Simplified functional schema
The future of professional encryption
End-to-end encryption is fast becoming a standard requirement for organisations intent on safeguarding their digital comms. However, not all solutions are equal—this technology demands technical expertise and a firm privacy commitment.
Innovations like Cryptoner demonstrate that encryption can be secure, high-performance and user-friendly.
For businesses, public bodies and institutions, adopting E2EE is not an option—it is essential. It ensures sensitive data stays protected and communications remain under your control.
Choose security first with Whaller
End-to-end encryption is more than a security feature—it’s a must for any organisation committed to safeguarding its internal communications. By choosing a collaborative platform like Whaller, you’re opting for a sovereign, secure and compliant solution that meets rigorous data protection standards.
To learn more about Whaller’s encrypted spheres:

Join us: to learn how Whaller can transform your organisation’s digital collaboration,
visit our website or contact us today.
📖 Learn more: Digital Transformation and Product.



0 Comments